- Google Workplace Single Sign On
- OIDC - OpenID Connect - supporting many other services including Okta and Azure Active Directory
Okta Configuration
-
Go to your Applications and create a new Application with the following settings:
- Sign-in method: OIDC - OpenID Connect
- Application type: Single-Page Application
- Under General Settings, make sure to select Grant types of Authorization Code and Implicit (Hybrid)
.png?fit=max&auto=format&n=ZKZPoQzuJb9d_Mqc&q=85&s=d6abe0679f179d03a688ef0e2433b783)
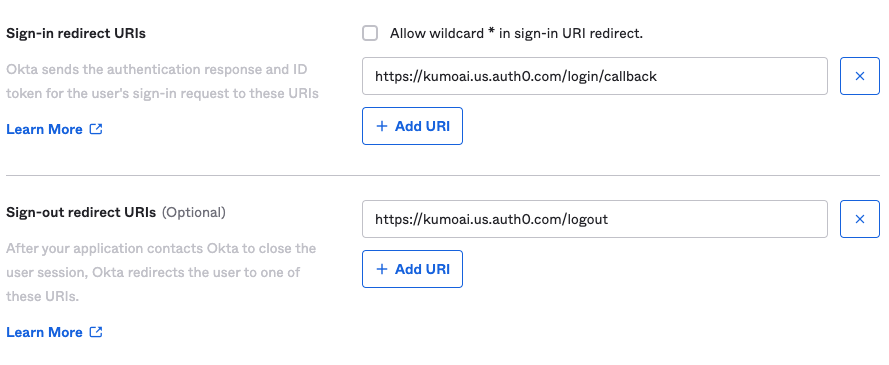
- Next, add the following sign-in and sign-out URLs
- Sign In: https://auth.kumoai.cloud/login/callback
- Sign Out: `https://auth.kumoai.cloud/logout
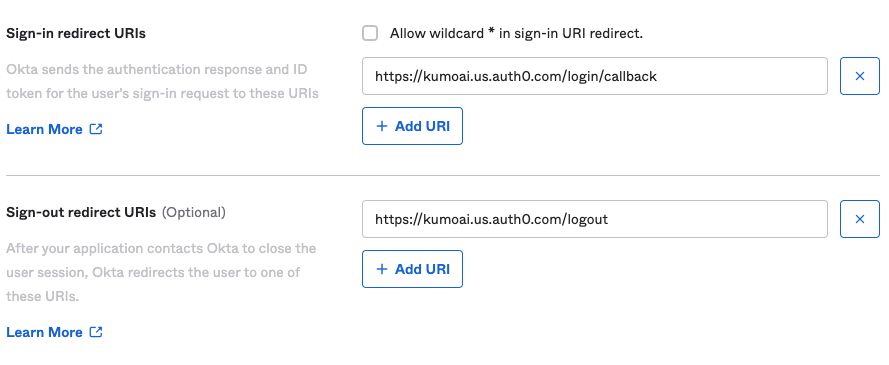
NOTE: Please use auth.kumoai.cloud instead of kumoai.us.auth0.com as shown in the image above
- Select your preferred Assignment policy
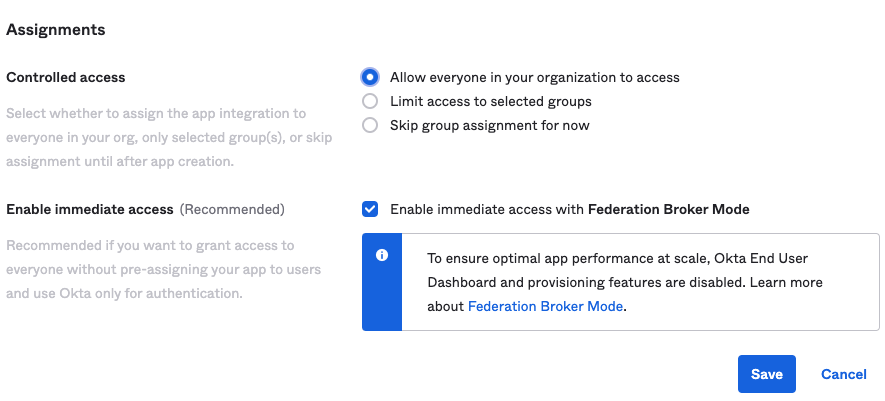
- Click Save to create the App!
- Copy the Client ID and your Okta base URL
- Example Client ID:
0oa654ok0jBdIJrpT5d7 - Example Okta URL:
dev-22499602.okta.com
- Example Client ID:
copy.png?fit=max&auto=format&n=ZKZPoQzuJb9d_Mqc&q=85&s=356333279716781b4add1a00074cf9c1)
- Send your Client ID and Okta Base URL to the Kumo team
